Impacts of Cyberattacks on Businesses
Do you know a cyberattack can destroy your entire business overnight? In the survey report of 2019, 64% of companies faced web-based attacks, 62% experienced phishing as well as social engineering attacks. Around 59% of the companies experienced to have received malicious code and botnets. Whereas, 51% of businesses experienced the denial of service attacks. (Source: TradeReady)
According to Cybersecurity Ventures, cybercrime damages will cost the world $6 trillion by 2021. In fact, 63 cybercriminals who come under the most wanted list of FBI are known to have committed a chain of cybercrimes that had cost people and organizations, billions of dollars.
Cyber attacks have become common and more endangering nowadays, irrespective of the scale or size of the business. It is important to have proper security of defense locks but, it is more crucial to know what is the cause of offense. The offense could be the existing security loopholes in your enterprise, the unprotected IT infrastructure, and vulnerable employees. All these problems can lead to destructive consequences which can compromise your data and can give rise to cybercrimes.
Furthermore, every individual working in an organization is required to be aware of the major cyberattacks that are endangering and big cyber threat postures. Here is the list of 6 major types of cyberattacks:
Types of Cyber Attacks
1. Phishing
Phishing is a social engineering attack that is deployed over internet users with the intention to steal their data including credentials and credit card details. It is an identity theft to dupe victims into opening the email and lure them to click on the malicious attachment in the email message.

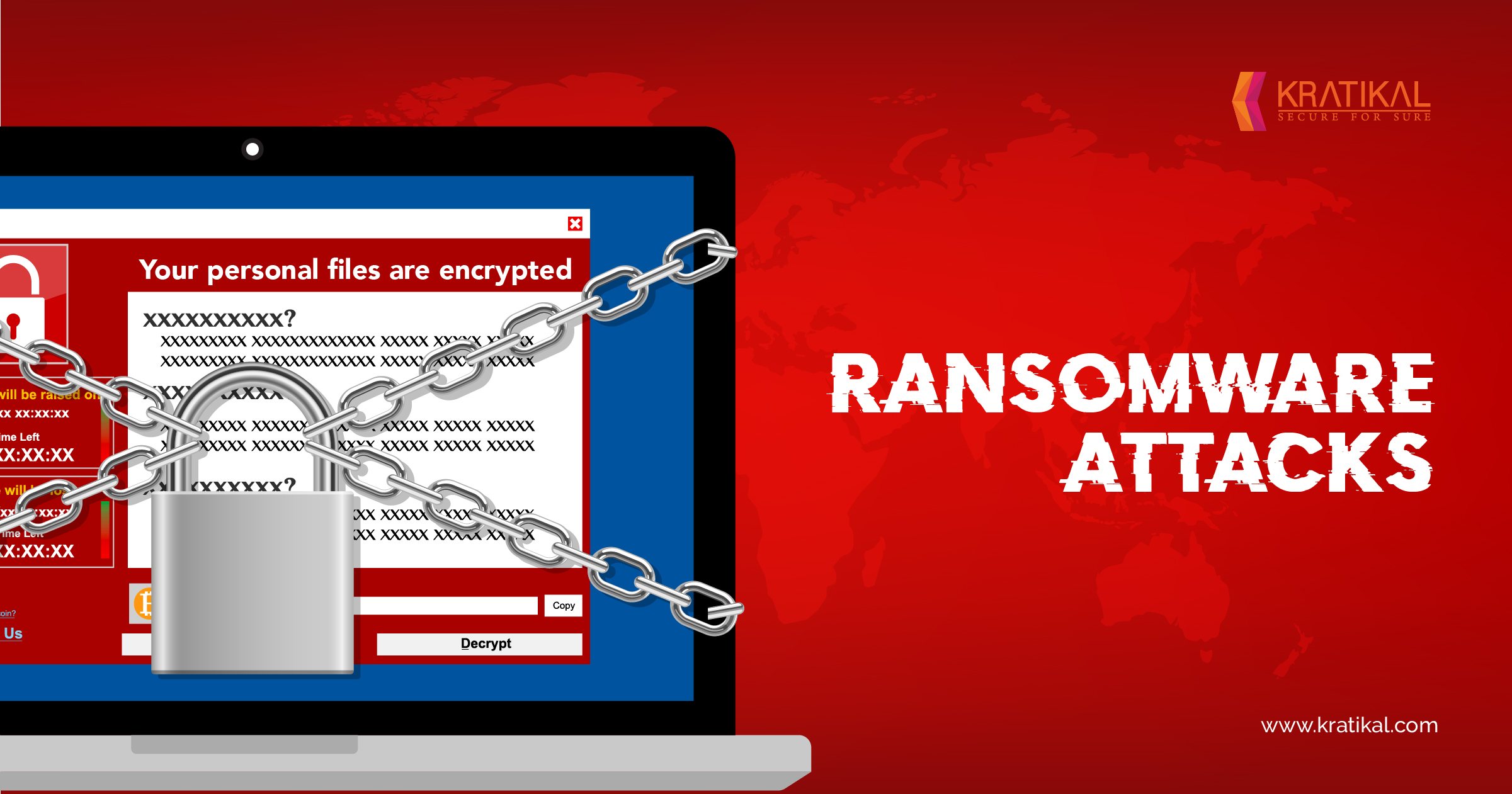
2. Ransomware
Ransomware is a type of malicious software, designed to bar access to a computer system or a data file until the user pays ransom to the attacker. While regular ransomware locks the system, a more advanced malware uses a technique named cryptoviral extortion attack that encrypts the files of users making them inaccessible until a ransom is paid to decrypt them.
3. Risk of Removable Media
Removable media like USB flash drives, external hard drives, optical discs, memory cards, digital cameras, etc. could be the bearer of cyber threats. These external portable storage devices are designed to be inserted and removed from a computer system. The usage of these devices could create a risk of data loss in case the media is lost or stolen. Further, it could lead to the compromise of a huge amount of data loss which would directly lead to damage to business reputation as well as financial penalties. Apart from that, removable media can be majorly used as an attack vector for malware.

4. Cyber Scam
Cyber thieves use the internet as a weapon to deploy cyber attacks on every scale of enterprises. These cyber scams come in various forms, including emails attempting to trick users into handing over their personal information over phishing sites or counterfeited web pages. It is a type of internet fraud where cyber attackers hide or provide incorrect information to trick victims out of money, property or confidential data.

5. Vishing
Voice phishing is a phone fraud that uses social engineering over the telephone to get access to user’s personal and financial information. The fraudsters use modern practices like caller ID spoofing or automated systems to sound like a legitimate authority overcall. Vishing is typically used for stealing credit card numbers or related information with the help of identity theft.

6. Smishing
SMS phishing is a fraudulent activity that is attempted to acquire personal information like passwords and user details by impersonating as a trustworthy identity. This social engineering technique involves cell phone text messages to deliver the bait to indulge victims to divulge their personal information on the attached link in the text message.

How to prevent Cyberattacks?
Cyberattacks seem to be constantly evolving every year and with major ransomware attacks like RobinHood, Snatch, Dharma, etc. in 2019, it is much clear that there is no slow down in the growth. But it’s never too late to secure your organizations by taking essential and efficient preventive steps to combat these attacks from any future loss.
With the help of cyber attack simulators, an organization can not only train but also make the individuals working, become proactive towards the prevailing cyber risks. Apart from that, it is necessary to make employees working in an organization, have the knowledge and are updated on the cyber threat postures existing.
Cyber attack simulators help not only help in identifying the level of vulnerabilities but also improve it so as to create a defensive system by strengthening the weakest link in the organization.
Along with cyber attack simulators, it is important to have a back up of critical data. By having critical backups of your data, you can allow only limited interruptions to the business workflow. It’s better to start securing your business by investing in the right cybersecurity solutions rather than paying for losses by becoming victim to cyber-attacks.






