On one hand, while the world is struggling with the pandemic COVID-19, another struggle is going on. Offices are now vacant and people are working from home. Employees do matter and so does the business. This is the reason behind the worldwide active adoption of ‘work from home’ culture.
However, work from home culture has its own drawbacks. Offices are secured with strong cyber security infrastructure along with a dedicated security team that monitors suspicious activities. Even after such stringent monitoring, cyber attacks still occur on organizations. One can imagine how vulnerable cyber security becomes when employees work from home.

In research conducted for the month of February and March, it was realized that there was a whopping 600% increase in cyber threats related to the COVID-19 pandemic. 40% of companies which enabled work from home policy for employees reported an increase in cyberattacks.
Simple Security Measures for Employees to Safely Work from Home
1. Provide cyber security awareness to employees
Employees must be provided with the knowledge to identify cyber-attacks such as awareness against phishing emails, risks associated with the use of public Wi-Fi, to ensure the security of the devices being used for work.
2. Secure medium of communication
Always use a secure medium of communication for official purposes. Make sure that security protocols such as DMARC are set in your email domain to secure it against any attempt of spoofing or abuse.
3. Deploy a phishing incident response team
In such a critical time when businesses are being hit hard, neglecting security can be an extremely dangerous situation for any organization. Every single effort matters and each form of vulnerability has to be taken into consideration. Since the majority of cyber attacks occur via emails. Therefore, a Phishing Incident Response tool is the need of the hour. A single vigilant employee can save the entire organization. A phishing incident tool empowers employees with the capability to report suspicious emails.

4. Deploy a VPN
Deploy a VPN for secure data transfer between the core system and work systems that employees are using remotely. It adds on as an additional layer of security by encrypting data while travelling.

5. VDI
Virtual desktop infrastructure (VDI) allows employees to work in a virtual environment as if they are connected to company’s local network from any place, at any time and from any device that is connected with the Internet. With VDI, data is stored on a server rather than the individual system. Not only does it significantly lower down risks to data but also, a lesser amount of bandwidth is required to store it.
6. Encourage employees to use cloud services
Encourage employees to use cloud services like doc, spreadsheet, etc. since this minimizes the risk to data as it is not stored locally.
7. Deploy an MDM solution
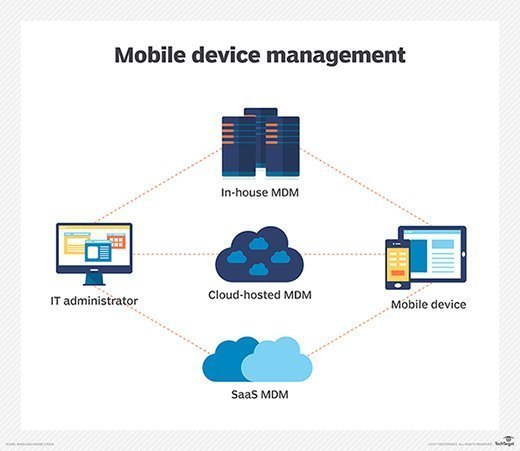
Deploying an MDM solution helps the organization in retaining control over business-related sensitive data. The solution allows administrators to remotely lock the devices and wipe all the data in case the device gets stolen. This prevents sensitive data from falling into the wrong hands.
Do You Want to Keep Your Organization Secure?
We are providing a 30-day free cyber health checkup for your organization. This will consist of free cyber security consultation and solutions including:
- SaaS-based email authentication and anti-spoofing solution KDMARC
- Anti-phishing, fraud monitoring & take-down solution KPMonitor
- Phishing incident response tool TAB
- Risk detection & threat analysis and
- Code risk review.
Let’s pledge to support each other in these difficult times and make sure that the human race survives and thrives once again!






