
What is Smishing Attack?
If you believed that phishing could be the only possible threat to cyber-security, then you need to hit the rock bottom! Cyber-attacks are expanding like spider webs over the internet to create havoc in the security system of various sectors across the globe. Just as a phishing attack, a smishing attack is a type of cyber-attack which is infamously trending and carries advanced techniques to obtain victim’s data.
Smishing is a blended word, made with the combination of SMS and phishing. Just as cyber-criminals use emails to phish people into opening malware-laden attachments, smishing attacks are carried out using text messages.
SMS phishing or smishing is an unethical practice of sending fraudulent cellular texts to users to trick them into downloading the attached file or redirected link. These attached links take users to malware-laden websites on their mobile phones.
Smishing text messages contain absurd phone numbers or links to lure customers for immediate response. Smishing attack on your cellular device can be deployed in any form of attention-seeking text.
These nefarious text messages could claim to be your bank asking for your financial information. It could also ask in a tricky way for your ATM number or account details to get access to your bank balance.
Recent Smishing Attack Example:
Just like phishing, smishing attack is deployed using cellular text messages with the motive to lure customers into giving away information. Smishing text messages often contain URLs or phone numbers.
The phone numbers usually have an automated voice system as a response. When it comes to SMS phishing, attackers use smart ways to trick victims into believing the text message they receive.
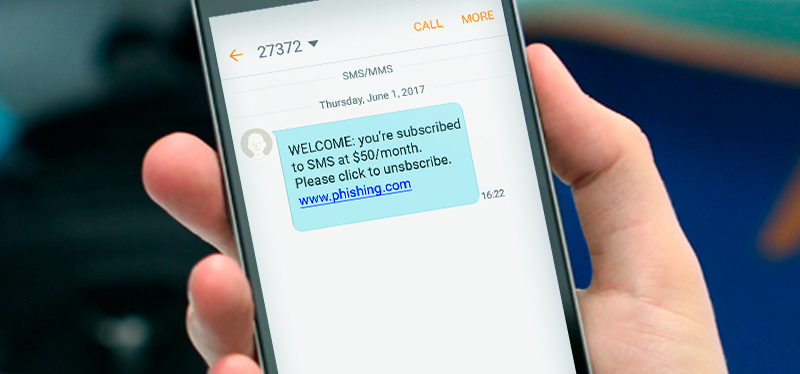
For instance, if a smishing message comes from a number “5000” instead of any actual phone number, it means it is sent through email on the cell phone. This is done to indicate a legitimate message to trick people.
In an article by Cyware, a smishing campaign, “Lucky Draw Campaign” was targeted on Indian Nokia owners. In February 2019, Nokia owners received a text message claiming they have won a lucky draw.
The message was impersonated to have come from ‘Nokia.com online shopping Pvt Ltd.co’, claiming that the recipient has won Tata Safari or Rs.12, 60,000. However, it urged recipients to pay to 6,500 Indian rupees to claim their prize.
How to Prevent Smishing Attacks?

- Never click on any links in text messages which come from unknown resources.
- Restrain from responding to personal text messages that ask for your personal details.
- If a text message looks like an alert or shows any urgency, verify the legitimacy of the source first before responding.
- Look out for messages that are no sent via phone number. Scammers often mask their identity so that their location or identity could not be traced.
- Messages that might be sent at odd hours or apart from business hours are usually smishing attacks.
- Never give away your bank details or financial information easily to any text message asking for your credentials or verification.
- Cyber Security researchers highly recommend organizations as well as individuals to use good security awareness tools as a preventive measure.


![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2019/10/Data-Privacy-vs.-Data-Security.png)






