
Fuchsia is not a Linux based OS like Android and Chrome. Android is primarily designed for smartphones and touchscreen phones. Fuchsia has focused on voice control and AI. It is designed to better accommodate voice interactions across devices. It has extremely fast processors and uses non-trivial amounts of RAM.
There are mainly two reasons why Google is working on a new operating system-
- Unlike Android and Chrome OS, Fuchsia is not based on Linux—it uses a new, Google-developed microkernel called “Zircon.” With Fuchsia, Google would not only be dumping the Linux kernel, but also the GPL: the OS is licensed under a mix of BSD 3 clause, MIT, and Apache 2.0
- People love to write cross-platform frameworks for two reasons: First, they want to run their apps to run on both platforms without doubling the effort. And second, because Android programming is still so painful even after the Kotlin.
About Fuchsia
- Fuchsia is based on newly developed microkernel called Zircon. The microkernel is basically a stripped down version of a traditional kernel (the core of an operating system that controls a computer’s underlying hardware).
- Fuchsia, is partially written in Dart which is an open source programming language developed by Google itself. Dart compiles to JavaScript.
- The fuchsia interface is written in Flutter SDK which is cross-platform and is also developed by Google.
- Fuchsia has a new UI called Armadillo that has a different home screen containing a home button, a keyboard, and a window manager. It supports vertical scroll system where the user can adjust other icons like battery, profile picture, weather report and so on accordingly.
- A user can also adjust the apps which are shown in the cards on the basis of how frequently or recently he/she is using the app.
- Armadillo can run on iOS and Android platform or any other platform that flutter supports easily.
- Google hasn’t made any public, official comments on why Fuchsia exists or what it is for but as per their documentation it will overcome all the shortcomings of the previous operating systems and will provide the high performance which is not possible to implement in the existing operating system (Android).
- The Fuchsia interface is written in Flutter SDK which generates cross-platform code that runs on Android and iOS.
Armadillo- The Fuchsia System Interface
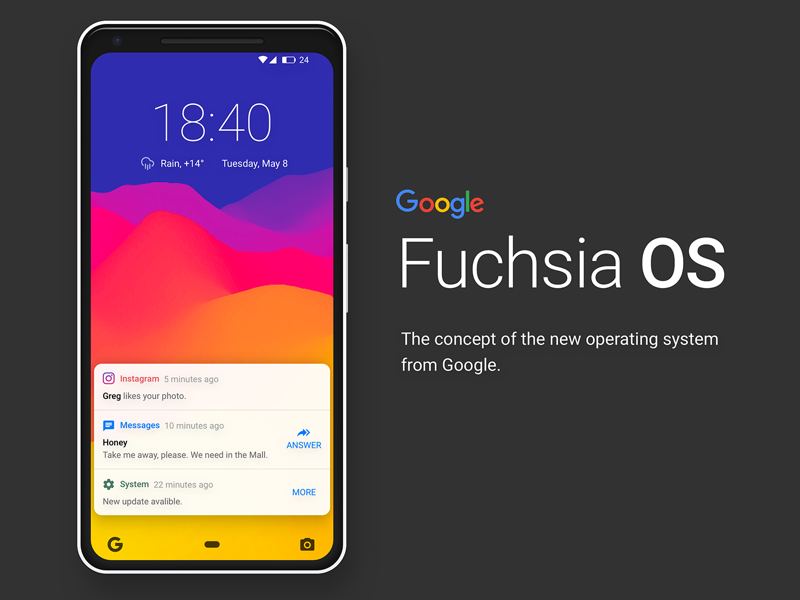
- Earlier, Fuchsia was based on commands but later its interface is designed in the language called Armadillo by Google which is pretty interesting now.
- According to the picture of its UI- here is the description of how things will work in case of Fuchsia.
The center profile picture is a clickable area that will open the menu which is similar to Android Quick Settings. Battery and connectivity icon will be shown on the top bar. There is also a horizontal slider for brightness and volume and also icons for do not disturb, auto rotate and airplane mode.
The bottom ‘Google Now’ panel will bring up a keyboard which is not the Android keyboard but instead it’s a custom Fuchsia keyboard which has the dark new theme. Fuchsia keyboard functions are different from Android keyboard.
Summary
So Fuchsia is a brand new Google project which may be the answer to “How we will start writing Android again if we need to end the era of earlier stable OS”.
The biggest challenge to bring the brand new OS might not be developing the new OS but the risk in the transition idea from the world’s most popular Android Operating system to the new one. We can not say anything about the future of the Fuchsia. It can be successfully launched to the consumers by 2020 as quoted by some source or can be entirely trashed by Google before it sees the light of the day.





![How to Backup VPS [5 Tips to Make it Simple] | Liquid Web](https://www.liquidweb.com/static/23275648d122433034250535983fe731/2f1b1/how-to-backup-vps.jpg)

