Will this year be as tumultuous as 2020? Let’s hope not. But one thing won’t change: In 2021, as is the case every year, companies will continue to be challenged by new or evolving cyber security threats.
We expect 5 security trends that emerged or accelerated last year to demand even more attention from organizations this year. Here is a look at key threats, potential vulnerabilities and defense strategies in 2021:
Zero Trust becomes more relevant than ever
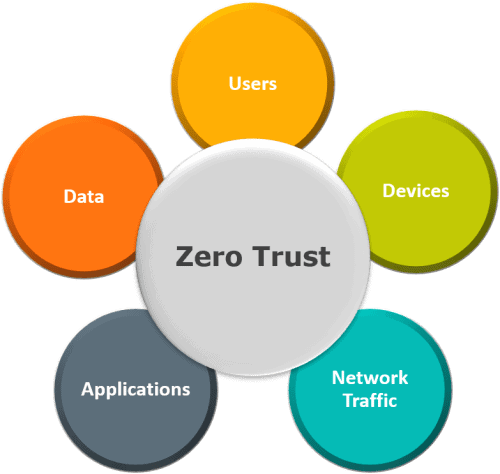
While the concept of Zero Trust has been around for over a decade, only now is it becoming a viable defense strategy. Today, every endpoint including remote PCs, smartphones, tablets, IoT sensors, containers, virtual systems and cloud resources is susceptible to attacks.
Traditional defenses are meaningless in an environment where the traditional network perimeter is slowly dissipating. It’s not just a matter if these assets will be compromised, but when. The only safe response is to trust nothing on your network and assume the environment is compromised. The premise of Zero Trust management is that to be secure, organizations must verify and authenticate access in a continuous manner.
In 2021, the rise of machine learning is paving the way for Zero Trust. Machine learning can be used to help document baseline user behavior and detect anomalies in actions. For example, if you normally log in from London, but today you’ve logged in from Hong Kong, the system recognizes this anomalous behavior, blocks access and triggers an alert to raise an investigation.
Applying Zero Trust will become an integral part of every organization’s business behavior as a way to future-proof the protection of data and assets.
Remote working is your new threat vector

As a result of government-mandated stay-at-home orders, remote working grew faster than anyone could have foreseen in 2020. Approximately 40 percent of the global workforce shifted to working from home or other remote locations. What’s more, the transition happened practically overnight and is expected to settle into a long-term trend.
Traditional security strategies, developed for staff working in the office within the same corporate network, are insufficient. In many cases, home routers and networks are not secure, and family members’ computing devices may be easily compromised.
What’s needed in 2021 is a new way of operating to work securely from remote locations. It will require changes in behavior, such as keeping access to corporate data from a home network to a minimum. Organizations must verify access to data and assets using various authentication methods that require human intervention and leverage new technologies, such as remote browsing or remote terminals, where no actual data is transmitted to the computing device at home.
Such changes, once unthinkable and impractical, will be crucial to securing work-from-home environments.
5G wireless offers new opportunities, enables new threats
After being touted for years as wireless networking’s next big thing, 5G is finally becoming mainstream. Apple introduced its first 5G-capable iPhones in late 2020, and telecom providers worldwide have rolled out 5G services.
5G computing with its high-speed connections and improved network reliability should empower organizations to quickly deploy compute servers, IoT sensors and other devices on the edge in remote hubs.
The features of 5G, however, can pose new threats if not well-managed. If infrastructure is not carefully secured, adversaries can exfiltrate information very quickly and in large amounts from compromised environments, thanks to 5G’s blazing-fast bandwidth.
Another concern is that most endpoint devices are not designed to deal with a high-volume network, which means adversaries could use 5G bandwidth to easily overwhelm network assets through denial-of-service attacks.
Ransomware moves one step ahead

Ransomware dominated headlines in 2020 and security experts have developed new tactics for responding to these threats. For example, by studying ransomware campaigns, security teams can deduce the decryption keys needed to unlock systems without having to pay the ransom.
Cyber criminals are aware of such countermeasures and are already developing ransomware encrypted at the code level. This means cyber security teams will have to wait for the code to run before it can be studied, thus slowing the development of countermeasures.
Attackers are also rewriting ransomware code to infect the firmware of computing devices and ensure perpetual presence in the victim’s environment. Code that is running at the firmware level may not be detected, stopped or removed by antimalware software.
As this malware cannot be simply overwritten, once a device is infected, the hardware must be either replaced or sent back to the factory to reinstall the firmware.
Cyber analytics drives more data-driven decisions
Organizations are starting to understand the importance of using data to improve business decisions. Operational data can give insights about potential growth and cost-savings opportunities, and how to optimize business process.
Security operations, like other parts of business, are harnessing operational data to understand how business events tie to security events. Organizations can use cyber analytics and AI to predict when and where attacks are most likely to occur so they can then focus their investments to achieve the greatest protection.
AI systems must target aspects of operations unrelated to security that can be correlated with past security events. For example, an AI system might determine that most attacks occur 3 days before quarterly financial results are due to be publicly reported. With that information, organizations can proactively bolster security protections prior to the next public disclosure.
In 2021, such pre-emptive knowledge will help organizations plan ahead. However, to succeed they must thoroughly analyze and understand all the data they collect about operations and business behavior.
Thankfully, 2020 is behind us, but new threats await. Protecting enterprises this year will require new cyber defense strategies and tactics, and better threat intelligence.

























:quality(80)/granite-web-prod/72/05/7205959f451f4c2891c6707b719a7377.jpg)