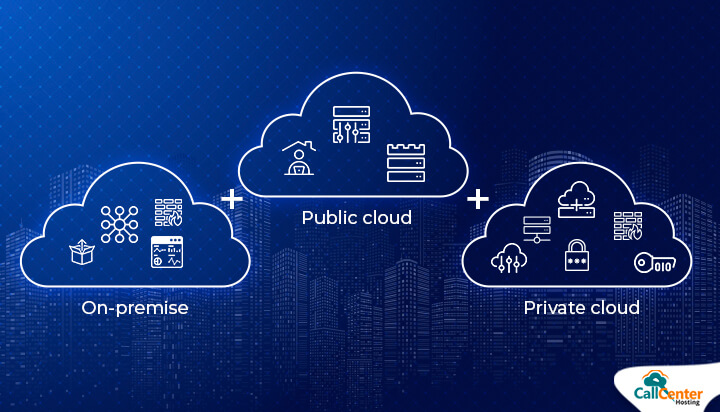
Multi cloud computing, where multiple cloud services are put to use to create a single overarching infrastructure, is becoming increasingly popular amongst larger enterprises. Many companies already use more than one cloud provider and over 30% of them use upwards of four. By the end of the decade, it is believed nearly all enterprises will have adopted a multi cloud strategy of some kind, as it gives them greater flexibility and even more potential for rapid innovation and deployment.
However, with other possible options available, such as developing a hybrid cloud infrastructure, it is important that those who make the decisions are fully aware of the advantages and disadvantages of adopting a multi cloud strategy and in this post, we seek to highlight what these are.
The advantages of multi cloud

By far the main benefit of creating a multi-cloud infrastructure is that it provides enterprises with the flexibility needed to innovate at speed. The reason for this is that it doesn’t tie them to the specific set of services provided by individual cloud providers. As a result, the way an enterprise chooses to innovate its own applications and services is not restricted by the limitations of a single host.
If a company relies on a single host, it may find it is adequate for the vast majority of its needs. However, if using that host means the company needs to make compromises on development then its innovations may end up being curtailed. Rather than go through the trauma of migrating all its services to another host that can help it innovate in the way it wants to, multi cloud enables it to run different services with different providers, each one offering the most advantageous platform for its specific workload. In this way, a multi cloud infrastructure is the best solution for developers looking for platforms that meet the specific needs of individual applications or services.
One example of this could be with GDPR compliance. An enterprise that uses cloud services based outside of the EU might find it easier to comply with GDPR if it used an EU based provider for the storage and processing of data pertaining to EU citizens. Another example is with performance. Using a cloud provider with a datacentre in a particular geographical location could improve performance within that region simply because of its proximity to users.
Another advantage of multi cloud is its ability to cut storage costs. Despite the price of data storage coming down, the ever-increasing volumes of data being collected means enterprises are still spending significant amounts on storage. However, the competition between providers that forces prices down means that those with multi cloud infrastructures can easily shift their data to the cheapest provider whenever prices change.
The final benefit of a multi cloud strategy is that it reduces the potential for vendor lock-in. The main risk here is that an enterprise can become dependent on the technology employed by a particular provider. However, by making the appropriate choices when developing an infrastructure and finding another provider where a compatible, redundant platform can be created, this can be overcome.
The disadvantages of multi cloud

The obvious disadvantage of using a multi cloud infrastructure is that the wider the range of cloud services an enterprise uses, the more complex it gets to manage. Failure to manage the system adequately can increase the costs of using such a system and could affect business agility.
One critical area which needs to be managed effectively is security and a multi cloud strategy can make this more challenging. By using a variety of public cloud services, the line of defence runs across more than one single provider, so it is essential that robustly secure networking and security measures are put in place. Areas which need close scrutiny include finding ways to monitor across different cloud platforms and ensuring that governance is comprehensive and robust.
A final issue with multi cloud is how to manage redundancy and high availability effectively and efficiently when using more than one provider. In instances where this is not efficiently managed, there can be the potential for financial wastage.
Conclusion
While multi cloud infrastructures are more complex and provide a bigger challenge for management, they do offer significant benefits. In a market where everyone is utilising technology to outpace their competitors, the need to innovate and deploy quickly can be the difference between survival and going under. A multi cloud infrastructure enables enterprises to remain a force to be reckoned with, providing the essential flexibility that is so crucial for rapid innovation.


 As
As