As businesses move more of their services on to web-accessible, cloud-based platforms, the need for robust security grows increasingly important. One key element of this security is controlling who has access to your data and applications. To strengthen security, reduce risk and improve compliance, it is essential that only authorised users get access to a company’s system and that authentication is required before that access is granted.
As businesses move more of their services on to web-accessible, cloud-based platforms, the need for robust security grows increasingly important. One key element of this security is controlling who has access to your data and applications. To strengthen security, reduce risk and improve compliance, it is essential that only authorised users get access to a company’s system and that authentication is required before that access is granted.
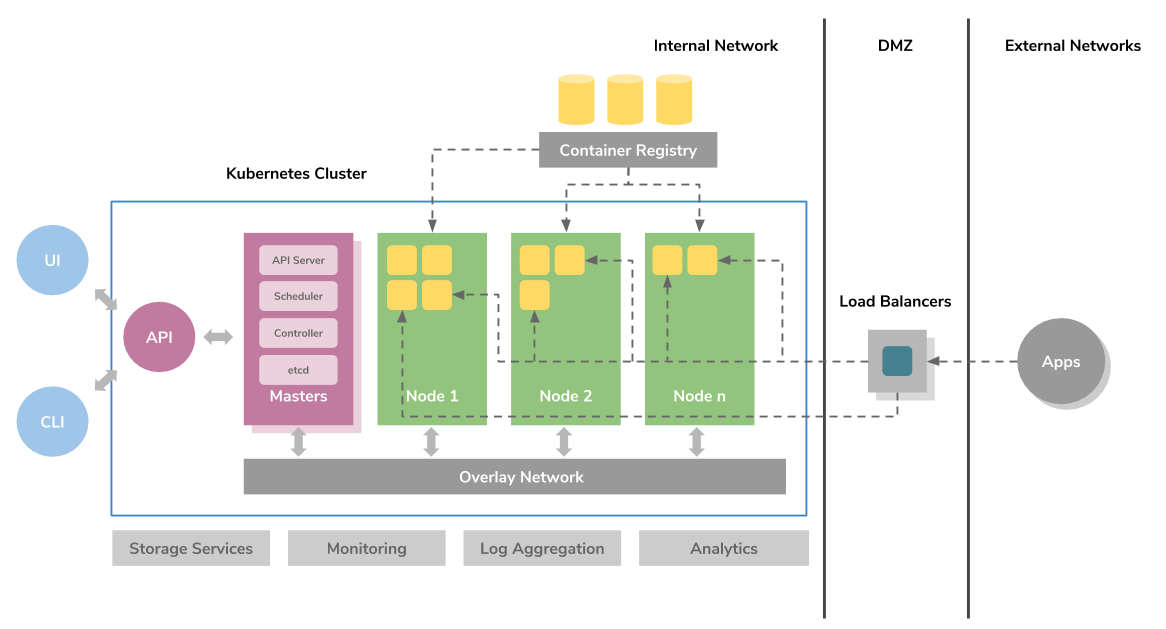
Cloud authentication explained
Cloud authentication is the means of verifying that someone logging in to a cloud-based platform is the person they claim to be. It is a way of preventing stolen usernames and passwords being used to log in to the system. The user’s identity is authenticated by cross-referencing information stored on a database with information held by the user, such as PIN numbers, biometric data or the use of secret questions. If the information provided by the user is identical to that stored in the database, authentication takes place and access is granted.
Authentication isn’t just required for people. Companies may also require external machine access to carry out automated services, such as cron-jobs, remote backups, auto updates and remote system monitoring. In these instances, too, it is crucial that external apps are authorised so that hacking bots disguised as genuine apps don’t slip through the security net. Authentication in these areas can be done through the use of digital certificates and APIs.
Authentication and authorisation

Authorisation is the granting of permissions for individuals to access different parts of a system. It is not desirable, in any organization, for every user to have the same permissions. Access to sensitive data, for example, might be restricted to only certain staff.
One of the advantages of authentication is that it helps prevent unauthorised users from accessing data they do not have the authority to see. In particular, it will stop employees who have forgotten their own passwords being able to log in using their colleagues account details and gaining access to all the areas they have permission to use.
Why authentication is so important
Preventing unauthorised access to cloud-based systems is vital. Hacked companies face enormous consequences: operational downtime, significant fines, potential lawsuits, reputational damage, industrial espionage and ransom. Customers can suffer just as much as companies too, with financial information being sold on the darknet and sensitive data being leaked across the internet. Lose personal data under GDPR and you could face a fine of up to €20 million or 4% of global annual turnover.
Authentication is a process which protects web-based systems from hackers and without it, your entire system is vulnerable. Cybercriminals use seriously advanced software that can crack usernames and passwords and they also use other techniques to phish for credentials from employees. Authentication provides an extra layer of security, using information that hackers can’t use. In this way, they are prevented from getting access.
Practical authentication

One challenge for businesses that use cloud-based systems is how to balance ease of use with strict security. Strong security is essential, but it can also be a hassle for users who need a quick and convenient way to log on. There is a range of different methods which can be used, here are two of the most common.
Two factor and multifactor authentication

To increase security, many organisations require two-factor authentication. This consists of a password plus one additional piece of information. Multifactor authentication requires a password and up to four other methods of verification.
There are four ways that a users ID can be authenticated, these are:
1. Asking for something the user knows, such as a PIN, date of birth or the answer to a secret question.
2. Using something the user has in their possession: customers may be required to get a code from a card reader or be sent a code to their smartphone.
3. Biometric data: the user may have to provide biometric data such as a fingerprint, photograph or retina scan.
4. Location data: smartphone GPS data and computer Mac addresses can also be used to verify the location of the user.
The need for strong authentication

The term ‘strong authentication’ is used to describe systems where authentication is robust enough to guarantee its security. What ‘robust enough’ means, however, depends upon the needs of the system, how critical its apps are, how sensitive the data it holds and the type of organisation it belongs to.
Some organisations may be adequately protected by two-factor authentication, however, for those with high-security requirements, multifactor authentication is the standard practice.
Many companies are now using smart card technology for authentication. Here, biometric data, passwords and other vital information is stored on a smart card and the card is used by inserting it into a reader and inputting a PIN. Contact less cards can also be used by tapping against an RFID reader. Lots of organizations use the same card to grant physical access to the companys premises.
Conclusion
Authentication is essential for organisations wanting to keep their systems and data secure, especially when it based in the cloud and can be accessed over the internet. To ensure your system is well protected, you should, as a minimum, use two-factor authentication. However, if you hold sensitive personal data or run critical applications online, then multifactor authentication may be the safest option.