What is SQL Injection (SQLi) and SQL Injection Attack?

If you are quite familiar with the cyber world then you must have probably heard of “SQL” or “SQL Injections” terms floating around. In simple words, SQL is a database language that stands for Structured Query Language. It was designed for operating database systems like MySQL, Oracle, Microsoft SQL Server or SQLite. On the other hand, SQL injection is a cyber-attack that targets the database with the help of specific SQL statements that are crafted to trick the system into performing uncalled and undesired tasks. The SQL injection attack changes the code to modify the command.
A successful SQL injection attack is capable of:
- Modifying, altering or deleting data from the database
- Reading sensitive and confidential data from the database
- Retrieving the content of a specific file present on the database management system (DBMS)
- Enforcing administrative operations like shutting down the DBMS
Without proper mitigation controls and security measures, the SQL injection attack can leave an application at a huge risk of data compromise. It can impact the data’s confidentiality and integrity as well as the authentication and authorization with respect to the application. It can also empower an adversary to steal confidential information like user credentials, financial information, or trade secrets by misusing the vulnerability existing in an application or program.
Types of SQL Injection Attacks
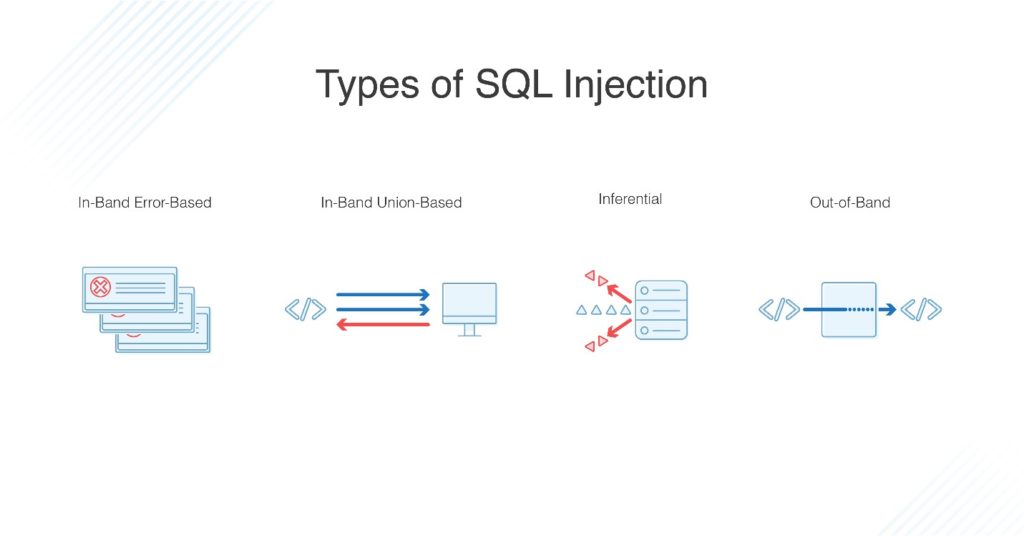
An SQL injection can be exploited in many ways and all of these ways require different levels of knowledge ranging from amateur to expert. Here are some common SQL injection types:
- In-band SQL Injection
It is the most common type of SQL injection attack in which the attacker uses the same communication channel for launching attacks and gathering their results. In-band SQL Injection is infamous among SQL injection attacks for its simplicity and efficiency. It has two sub-variant methods:
-
- Error-based SQL Injection: A technique in which the attacker determines the vulnerabilities of the system by deliberately causing the database to produce error messages. Later these error messages are used for returning full query results and revealing all the confidential information from the database. This technique can also be used for identifying vulnerabilities present in a website or web application and in obtaining additional information to redevelop malicious queries.
-
- Union-based SQL Injection: In this technique, the attacker gets the benefit of extracting information from the database by expanding results that are returned by the original query. But the Union operator is only useful in case the original or new queries have the same number and data type of columns.
- Inferential (Blind) SQL Injection
Blind SQL injections mainly rely on the server’s behavior and response patterns where the attacker closely observes the indirect clues. For this observation, the attacker sends the server data payloads. This type of technique is called Blind SQL injection because the attacker doesn’t get the data from the website database, thus making it impossible to see the information about the attack in-band. The Blind SQL injection is classified into two methods:
-
- Boolean: Here the attacker sends an SQL query to the database that prompts the application to return a result. However, depending on the query, true or false, the result varies, and based on the result, the information modifies or stays the same, that is there in the HTTP response. With the help of it, the attacker finds out whether the result is true or false in the message generated.
-
- Time-based: When an SQL query is sent to the database by the attacker, the database waits for some seconds to respond. By observing that period of time taken by the database to respond, the attacker gets to analyze whether the query is true or false. And based on that result, an HTTP response is generated either instantly or after some waiting period. Thus, without relying on the data from the database, the attacker can determine if the message used has returned true or false.
- Out-of-band SQL Injection
The most uncommon approach to attack an SQL server, this technique relies on particular features of the SQL-enabled database. It involves the submission of a DNS or HTTP query to the SQL server that has an SQL statement. If successful, the Out-of-band attack can transmit the contents of the database, escalate user privileges, and perform the same actions that other types of SQL injection attacks perform.
The Recent SQL Injection Attack Examples
Many SQL injection attacks have taken place in the past decade and it can be concluded that SQL injections are one of the most evolving types of cyber attacks. Between the years 2017 and 2019, the SQL injection attacks accounted for 65.1 % of all the attacks on software applications. Here is the list of top SQL injection attack examples of all time that every user must be well aware of!
- In one incident of an SQL injection attack, personal details of 156,959 customers were stolen from a British telecommunications’ company’s servers, exploiting a vulnerability present in the legacy web portal. (source: Wikipedia)
- According to Help Net Security, 60+ government agencies and universities were successfully targeted using SQL injection attack by a hacker who was involved in penetration of the US Election Assistance Commission and subsequent database sale in November 2016.
- The officials at Johns Hopkins University on March 7, 2014, publicly announced that their Biomedical Engineering Servers became victims of an SQL injection attack. The hackers compromised the personal information of 878 students and University staff. They posted a press release and the leaked data on the internet. (source: Wikipedia)
- In May 2020, a New Yorker was charged for hacking into e-commerce websites with the motive to steal credit card information. It was reported that the hacker along with its gang used SQL injection techniques for hacking into vulnerable e-commerce websites to steal payment card data.
How To Prevent SQL Injection Attacks?

In order to secure your organization and mitigate SQL injection attacks, the developers, system administrators, and database administrators in the organization must follow these below-mentioned steps:
- Ensure to keep all web application software components up to date with the latest security patches and leaving no place for vulnerabilities.
- Avoid using shared database accounts between different applications or websites.
- Regularly monitor SQL statements from database-connected applications.
- Limit the attack surface by getting rid of any database functionality that is no longer needed in order to prevent it from being misused by hackers.
- Error messages are key for attackers to learn a great deal about your database architecture, so make sure to display only minimal information.
- Always keep the database credentials encrypted and separate safely.
- Most importantly, these inculcate the practice of periodic VAPT, i.e. vulnerability assessment and penetration testing. A regular VAPT provides a detailed picture of exploitable vulnerabilities existing within an application and all the risks that are associated with these vulnerabilities. It allows IT, security teams, to focus on the process of mitigating critical vulnerabilities.
Do you think that the SQL injection attack can be another big threat to the next-generation-based software applications in the near future?