What is Cybersecurity?

While cybersecurity and information security may seem synonymous to users, both terms are theoretically different in the concept of security. Cybersecurity is the amalgamation of processes, technologies, and practices, chiefly designed to protect data, systems, networks, and programs from unauthorized access and cyber-attacks.
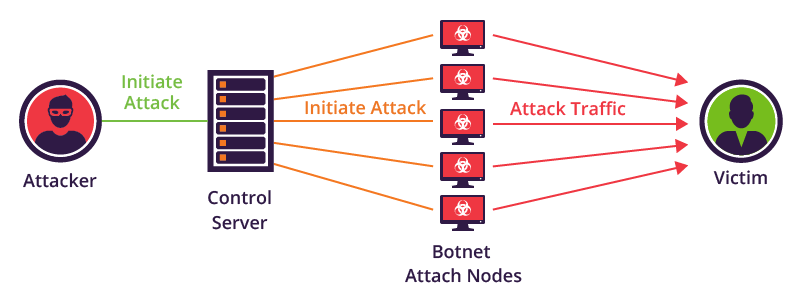
Organizations transmit sensitive and confidential data across networks and to other devices for business purposes on a daily basis. This is where cybersecurity plays the role of securing information and systems used for process or storage from various types of attacks in cybersecurity.
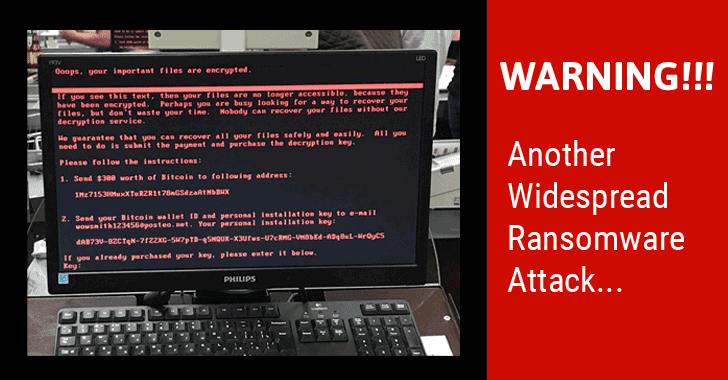
As ever-evolving cyber-attacks are rapidly on the rise, implementing cybersecurity solutions helps in safeguarding the data related to confidential and financial records of the company. Employee security awareness, training tools, incident response tools, email authentication protocols, brand monitoring tools, etc. are some types of cybersecurity solutions.
What is Information Security?

Cybersecurity explained above states the focus on the security of process and technology. However, information security is entirely a different concept. Information security plays a role in ensuring that both digital and physical data is being protected from unauthorized access, exploitation, recording, disclosure or modification.
The abbreviated term of information security is “infosec” and is also referred to as “data security”. It aims to keep data secure regardless of digital or physical form. Moreover, information security is a set of practices to keep data secure during scenarios where it is being stored or transmitted from one device or place to another.
While information security remains to be a primary focus in protecting the confidentiality, integrity, and availability of data, maintaining organizational productivity is equally an important concern. This is why information security offers guidance, security policies, industry standards in passwords, antivirus software and information security awareness to provide best practices.
So, if cybersecurity and information security work on the same goal of safeguarding an organization’s data, then what differentiates both terms? Let’s find out with the difference stated below!
Cybersecurity Vs. Information Security: 5 Key Differences
Before continuing to learn what differs both terms, it is important to understand that cybersecurity is basically a subset of information security. You can consider information security as an umbrella with cybersecurity coming underneath it along with other security standards.
Now let’s read further to figure out the differences between these two terms:
| Cybersecurity | Information Security |
|
|
From the above-given table, now we can easily differentiate between both the terms. While information security mainly concerns protecting data of organization from any sort of unauthorized access, cybersecurity ensures that an organization’s electronic data is secure from cyber threat actors. Cybersecurity is a broad practice of ensuring that servers, networks, and email channels remain protected and accessible to only authorized users that fall under the realm of information security.
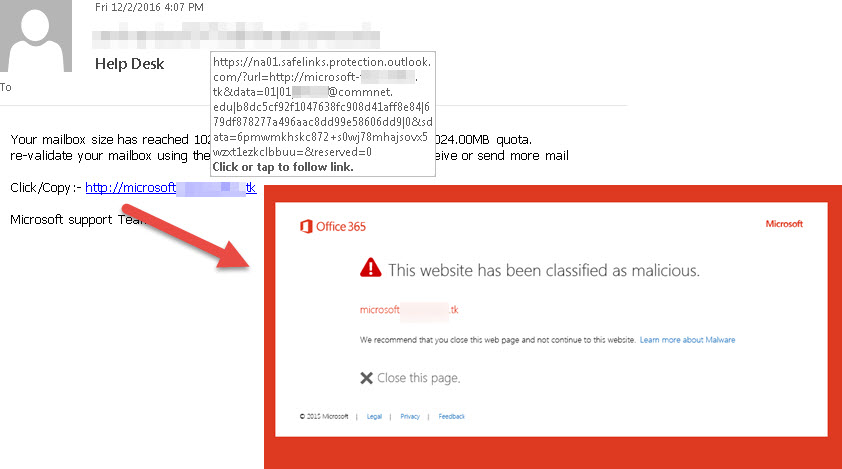
Although, the information is not the only area of concern for cyber threat attackers. Some hackers are keener about uncovering the user’s login credentials and gaining unauthorized access to closed networks. Their purpose to do so is to manipulate the data and website or hamper the essential functions.
To prevent hackers from attempting such malicious activities, patching up existing vulnerabilities in networks and devices is a must. Doing so leaves no room for hackers or cyber threat actors to make any possible interaction between the computer device and network or server.
This is why we have certain types of cybersecurity solutions that hold a wide scope right now. Moreover, the experts in this field will have high demand over the next decade too due to the introduction of new technology trends.
The Parallel-ground Between Cybersecurity & Information Security
After all these differences, you might wonder if there is any parallel-ground between cybersecurity and information security or not. Well, the answer is yes! Both cybersecurity and information security are the foundation to information risk management.
While cybersecurity professionals are mainly concerned with safeguarding electronic data from cyber risks and data breaches, they still perform physical security practices. Just like information security professionals keep a cabinet full of confidential information locked, cybersecurity experts require physical security measures to keep adequate data protected. It is impossible to physically lock a computer device, but having security protocols in place, one can easily prevent unauthorized access.
Both cybersecurity and information security are crucial aspects of technology in this evolving 21st century. Organizations looking forward to data security must understand the importance of these two aspects of technology. Every security administration of an organization must stay one step ahead of the ever-evolving security threats.
They are needed to provide and implement the best security awareness training practices and as well as analytical tools to monitor phishing and fraud activities taking place on the online platform. With constantly developing technology and the IT world, security professionals must stay updated to tackle down the evolving security risks and prevent future cyber threats.