- The complexity of their source code increases the chances of manipulation of the code with malicious intent and unseen vulnerabilities.
- These attacks can be launched easily and target multiple targets at the same time.
- The rewards reaped by the attackers are huge. They can get hold of the financial information or other private data that belongs to the users of the application.

Organizations need to be wary of such attacks on their web applications as it can result in the disruption of their relationships with their clients or can lead to legal action against them. According to a report published by Forrester in 2020, 35% of all external cyber attacks on organizations came in through a web application. In fact, Security Boulevard reported that as the first batch of COVID-19 vaccine vials was distributed, an increase of 51% web application attacks on healthcare targets was noticed.
Also, recently, a report by Business Standard revealed that a hacking group called ShinyHunters leaked 1.9 million user records stolen from an online photo editing application known as Pixlr. In another case, the same hacking group stole the data of users from an online dating website named MeetMindful.
All of this should be alarming for organizations, especially the ones dealing with sensitive user information. Web application security, an often ignored aspect of cyber security, should therefore be given priority in the cyber security policies of organizations.
Types of Web Application Vulnerabilities
Web application attacks can take various forms. This is done using different vectors mentioned below-
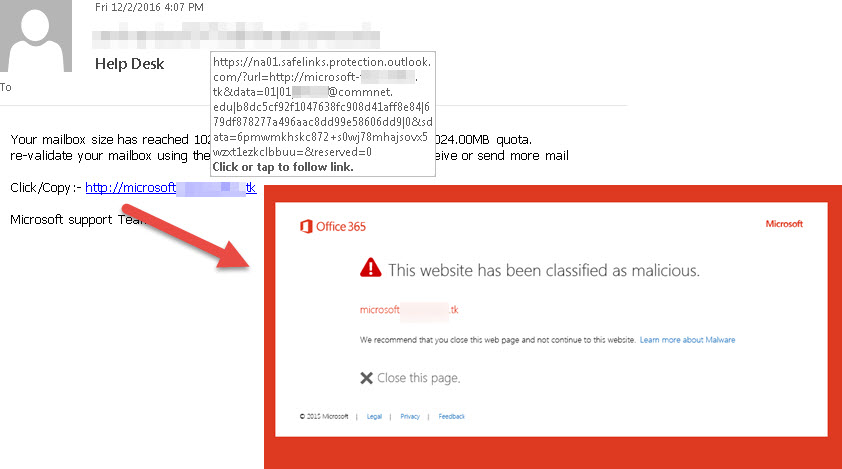
- Cross-site Scripting (XSS) – It is a type of injection attack that targets users to access their accounts, modify the content of a page or activate trojans. Direct injection of a malicious code into an application results in Stored XSS. A Reflected XSS occurs when a malicious script is reflected off an application onto a user’s web browser.
- SQL Injection – SQL Injection is a malicious SQL code used to manipulate a back-end database in order to reveal information. This can result in unauthorized access to the administrative control of the web application and unwarranted modification of data.
- Remote File Inclusion – Injecting a file onto a web application server from a remote location is known as Remote File Inclusion. Hackers use this vector for the execution of malicious scripts within the application. It has also been seen that this vector is used for data manipulation and data theft.
- Cross-site Request Forgery – This kind of attack takes place when a malicious web application makes a user’s browser perform an unwanted action on a site where the user is logged in to. This attack can result in an unsolicited transfer of funds, changed passwords or data theft.
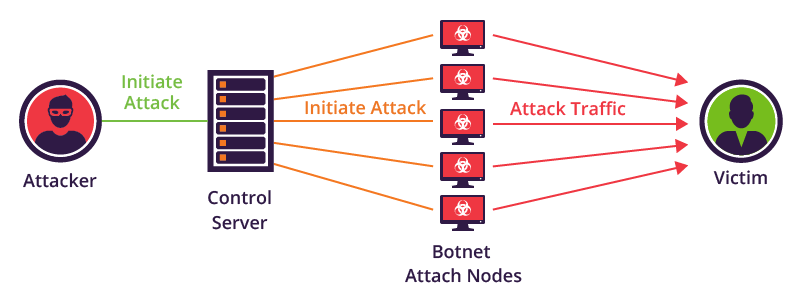
- Denial of Service (DoS) Attack – Denial of Service Attack (DoS) occurs when a server stops responding to the incoming requests of its legitimate users or starts responding very sluggishly due to its overloading with different types of attack traffic.
- Misconfiguration of Security Settings – Attackers pounce upon the chance of exploiting misconfigured security settings or settings that are set at default, verbose error messages with sensitive information and misconfigured HTTP headers.
- Insufficient Logging and Monitoring – This is one vulnerability that can help the attackers further attack systems or tamper, destroy and extract data. According to security experts, it takes 197 days on an average to detect a data breach.
- Buffer Overflow – Buffer Overflow is the overflowing of the buffer’s capacity, which is a space in memory, resulting in the overwriting of the adjacent memory locations with data. This can be used to inject malicious code into the memory.
Measures for Risk Mitigation
- Using a Web Application Firewall – A Web Application Firewall is a hardware and software solution designed to defend against any attack attempts. It is a good way to compensate for any code sanitization deficiency.
- Gathering Information – Classify third-party hosted content and review the application manually to identify client-side codes and entry points.
- Authorization – Test the application for missing authorization, insecure direct object references and horizontal and vertical access control issues.
- Encryption – Encrypt the specific data and avoid the use of weak algorithms.
- Bot Filtering – Mass-scale automated attacks are launched using malicious bots. This bot traffic can be detrimental for the web application and is therefore dealt with Bot Filtering tools.
- Conducting VAPT– VAPT (Vulnerability and Penetration Testing) is an essential service for organizations in their quest for safer use of IT infrastructure. VAPT is like a self-assessment service that brings the vulnerabilities related to the APIs, technology, platform, etc to the fore, thereby shaping the cyber security policies of the organizations and helping them upgrade their systems. Web application security assessment, therefore, goes a long way in ensuring the smooth functioning of the web application.

Apart from this, web application security is also necessary for GDPR compliance. If an application processes personal data of EU residents, then the GDPR requires that organization to follow security “by design and by default” for data protection (Art 25). It is therefore recommended that organizations running web services or web applications put the requisite cyber security measures in place to tackle any kind of attack