Did you know that the Android App Bundle has become the gold standard for publishing on Google Play? Dig into its benefits.
When I first heard about this new upload format known as the App Bundle, I was very excited! Many of the issues that we developers faced like building APKs to target different API versions, device types, and so on- are now passed on Google Play.
From this day on, developers will be able to use Dynamic Delivery for creating optimized APKs that satisfy the requirements of user’s devices and delivers them at the runtime for installation.
All this is being done through the Android app bundle app distribution format. Let us dive into what Android’s new, official publishing format is all about.
What is Android App Bundle?
Android launched a new official publishing format called android app bundles (.aab) and it offers a more efficient way to build and release your app. It also lets you easily deliver a great user experience in a small-sized app, this in turn also improves install success rate and reduces uninstallation rates.
Android App Bundles are Google recommended way for building, publishing, and distributing the application across different device configurations.
Did you know that the android app bundle has become the gold standard for publishing on Google Play? Over 600,000 apps and games currently use the app bundle in production, representing over 40% of all releases on Google Play including Netflix.
Let’s look into the benefits of app bundles now.
Benefits Of Using Google Android App Bundle
1. Size Reduction
App bundles help in reducing a significant amount of application size! On average, developers have witnessed a 20% size savings compared to APK. You can visit the new app size report in the google play console to see how much your app could save.
Did you know that, with the help of app bundle development, Adobe reduced the size of Adobe Acrobat Reader by 20%? Not only this, but some of these size savings by early adopters of app bundles show some jaw-dropping results. These results are what make Android app bundles a great way to build Android Go apps:
2. Increased app installations and decreased uninstallations

Apps increasing size would not matter much if we had unlimited storage in our devices. But, as we know, it’s not the case. As the size of an app increases the number of installations decrease!
As a ripple effect of size savings with the help of xamarin android app bundle will increase the app installations. This also resulted in the increase of update rates, and very fewer uninstallations.
3. Higher efficiency

App bundle development in android allows you to build one artifact that includes all of your app’s collected code, resources, and native libraries. So, you are no longer required to build, sign, upload, and manage version codes for multiple APKs. Hence, the efficiency is increased if you install an android app bundle on your device.
4. Faster downloads

Your app can be efficiently tailored to each device by Google Play which means the process of downloading and installing the app becomes faster.
5. Integrated codes

With the help of the android studio app bundle, you can prepare for the 64-bit requirement without increasing the size of your app. As a result, Play will deliver the appropriate native code required for each device.
6. Increased engineering velocity

The entire process of creating an app is accelerated. From building dynamic and independent modules to designing, testing, and releasing it. The engineering velocity gets a major boost with the android app bundle unity.
For example, The Book My Show app declared that their app builds time (for a completely new build, without any caching) went down by 70% — this is because, with app bundles, it just dumps every resource into the bundle, rather than segregating them, like for APKs.
7. Reduced manual effort

During android app development several manual efforts can be completely automated. Once the development is done, its link is uploaded and shared on a specific Slack channel automatically. No manual intervention is required.
8. Dynamic delivery enabled
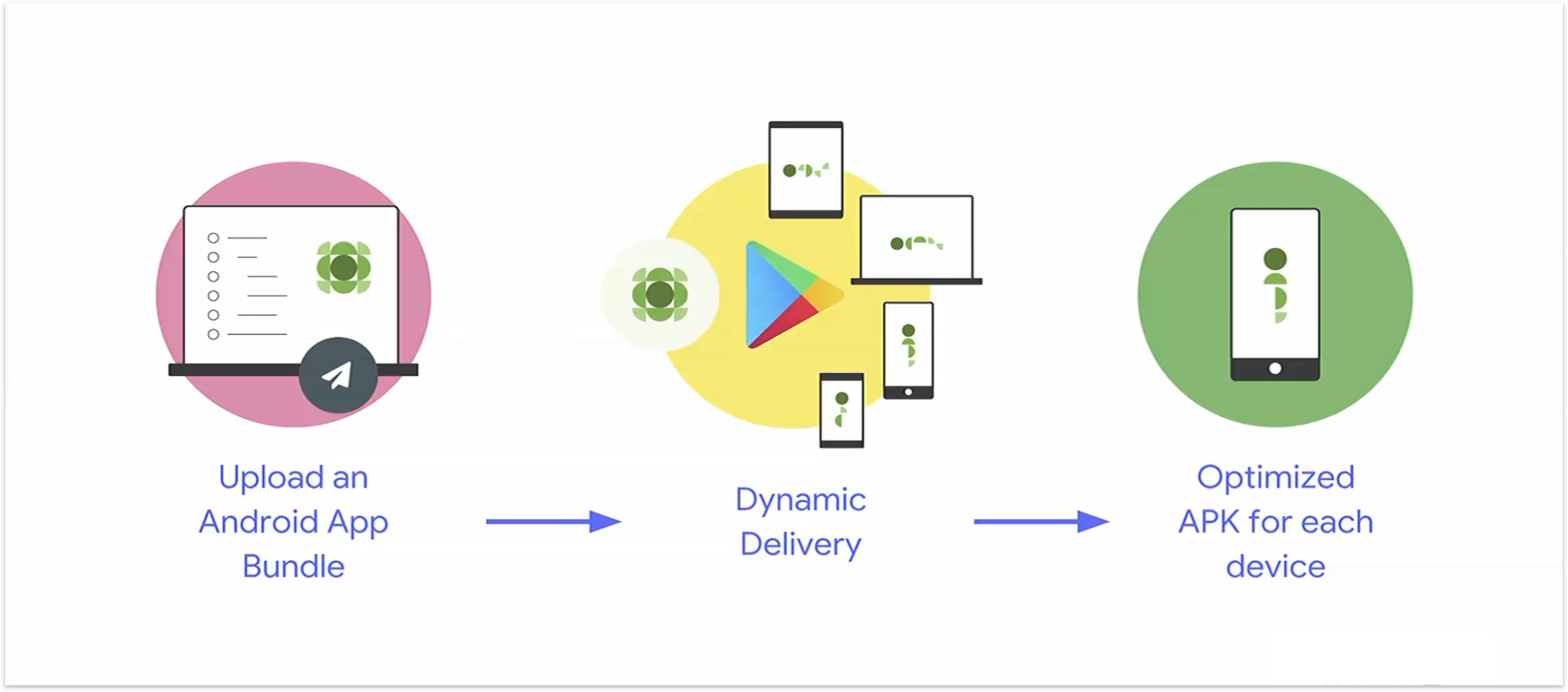
App bundles have introduced us to a new concept known as dynamic delivery. One can deliver conditional features at the time of installation on the basis of properties like device features (e.g., AR/VR), user’s country, or device’s version. Users are also given the facility to install features on an on-demand mode instead of the install time. They can even uninstall the features they no longer need.
This will help the users personalize their experience as per their requirements. This will also come in handy when you do not want to increase the size of your app in the long term. Further allowing us to make the initial size of our application smaller and then offering extra features only to the users who might actually make use of them.
How To Build and Deploy Android App Bundles?

Unlike APKs, app bundles are a publishing format that entails all of your app’s codes. So, it cannot be deployed directly to a device. With the help of the android studio, creating a project as a signed app bundle is just a few clicks away!
To build app bundles, follow these steps:
Step-1: Start with downloading Android Studio 3.2 or higher. It is the simplest way to build app bundles.
Step-2: Add support for Play Feature Delivery by including a base module, organizing code and resources for configuration APKs, and, optionally, adding feature modules.
Step-3: Now, start building an Android App Bundle using Android Studio. You can even deploy the application onto a connected device from the app bundle through modification of your debug/run configuration and selection of the ‘deploy APK from app bundle’ option.
Step-4: Testing and publishing your app bundle will be the final step.
Test Your App Bundle
Once you create the android app bundle, you should test how Google Play will use it to generate APKs and how those APKs will behave when deployed to a device. You can use the following methods to test the same:
- Test your app bundle locally by using the bundle tool. It will generate APKs from your app bundle and deploy them to a connected device.
- Share your app with a URL. It is the speediest way of uploading your app bundle and sharing your app as a Google Play Store link with your testers.
- Set up an open, closed, or internal test. This is another way of testing custom delivery options, like downloading app features on demand.
Final Words
The future has a lot in store for all of us and it is up to us to keep up with it! Without any doubt, I can tell you that the android app bundles are where the future lies. Being an android app development company, we can help you stay ahead in the game.








/getty_proofreading-184928153b-56afa02f3df78cf772c6cfb9.jpg)