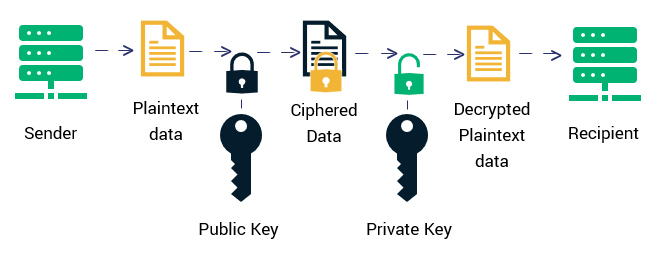
Familiarising With The Term Cyber Security

You must have heard of the word cyber security, making headlines in the news, internet, social media, IT forums, etc. However, has it ever occurred to you that what is cyber security or why does the security administrator of your organization keep on talking about the importance of cyber security?
Fundamentally, cyber security is the body of technology, process, and practice, designed to protect systems, networks, programs, and data from cyber risks like cyber attacks, damage, or unauthorized access. It is also referred to as information technology security. With cyber attacks evolving today as a danger to organizations, employees and customers, cyber security plays a very crucial role in prevention against such security threats.
As we have entered into this new decade, we can already see new challenges arising in cyber security since day one! It is no surprise to see that cyber security is constantly on a rise and there is a lot in store for the near future. Today, companies have become more technologically reliant than ever and the trend doesn’t seem to stop. Rather, it looks like this technological reliance will keep evolving in the long term.
Almost every organization nowadays, uses cloud storage services like Dropbox or Google Drive to store their confidential data and sensitive information. If not taken proper online security measures, this data present online can easily be exploited by cyber criminals.
Why is Cyber Security Important for Companies Today?

Often some organizations take their data security lightly and as a result, they fall victim to cyber attacks. In fact, our companies are still not immune to these evolving cyber attacks. But thanks to these fast-developing technology standards today, cyber security has become a priority for every organization across the world.
It is a serious matter of how cyber attacks are shaping in every form possible in order to stay one step ahead of the development in technology. Phishing, ransomware, cyber scams are some of the common yet highly dangerous cyber attacks that are designed with the motive to access and exploit the user’s sensitive data and extort money out of it.
Here are some more major reasons to understand why cyber security is important for companies:
- Rise of Cyber Crimes
Be it a large scale or a small scale firm, hackers and cyber criminals spare no one. Rather, they lookout for opportunities to exploit data and get money out of these firms. Over the past year, the average cost of cyber crime for an organization has increased 23% more than last year—US$11.7 million, according to the report. Also, the average number of security breaches has risen significantly and it is now $3.86 million, as per the report. With the introduction of new technologies, the chances of cyber threats and risks are also rapidly increasing. Cyber criminals have advanced their attempts of deploying cyber attacks with the evolution of technology.
- Growth of IoT Devices
With the mission to create smart cities with smart devices, our dependency to connect everything to the internet has increased too. The introduction of IoT technology i.e. Internet of Things, has not only simplified and speed up our tasks but has also created a pit of new vulnerabilities for hackers to exploit. No matter how advanced security measures we take, cyber criminals will always stay one step ahead to attempt cyber crimes. If these internet-connected devices are not managed properly then they can provide a gateway to business to hackers or cyber criminals!
- Bridge to Security Gap
Human resources and IT resources have always been one of the most important aspects of any organization. Regardless of their dependency on each other, there has always been a security gap between both aspects. In order to bridge this gap, it is important to provide individuals working in an organization with the right cyber security awareness training. Training for employees is necessary to bridge the gap of cyber security skills and to create a cyber-resilient working culture in the organization.
- Cost of Cyber Risks
Cyber attacks today are not only multiplying in numbers but are also multiplying in the cost of damage created. These cyber attacks can prove to be extremely expensive for any organization to endure if not taken proper security measures. With more business infrastructures connecting, it is predicted, cyber crime to cost the world $10.5 trillion annually by 2025, says the report. Besides, it is not just the financial damage that could cost but also the reputation of the firm along with loss of customer trust in the business.
- Security of Data
When it comes to data security, it can be clearly seen how organizations are getting highly comfortable in keeping their information online. With the alarming number of data breaches and information leaks making news headlines almost every day, it can be seen how vulnerable the data left is online. Moreover, cyber attack vectors such as ransomware, phishing, cyber scams, risk of removable media, etc. leave no room for data exploitation and publicizing of any vulnerable data. Implementation of the right cyber security solutions is a must to avoid any future cyber risks related to the sensitive data of an organization.
How to Cyber Secure Your Organization in 2021?

Are you here to look for the best defensive system for your organization to combat cyber attacks? Well, the only thing that is important for your organization in 2021 is a strong cyber security system along with the best cyber defense practices to reduce the cyber threat posture of your organization.
Solely relying on anti-virus software will not stop cyber criminals from accessing your business. But educating employees in making smart cyber defensive choices can definitely reduce the chances of cyber risks!
Moreover, it doesn’t require a specialist to teach employees about cyber defense and cyber security awareness. There are advanced technology-based tools available today to help and guide employees in recognizing and combating cyber threats before they infiltrate networks and systems.
The web and network attackers are constantly striving to undermine the security system of the company’s IT infrastructure today with the intention of stealing the confidential data. Thus, making it more challenging for organizations to stay cyber secure.
Organizations are required to equip themselves to prepare for tight security measures and best cyber security solutions like security risk assessment tools, anti-phishing, and fraud monitoring tools to look for vulnerabilities and to track your brand online. Always remember that an ounce of prevention is worth a pound of cure!