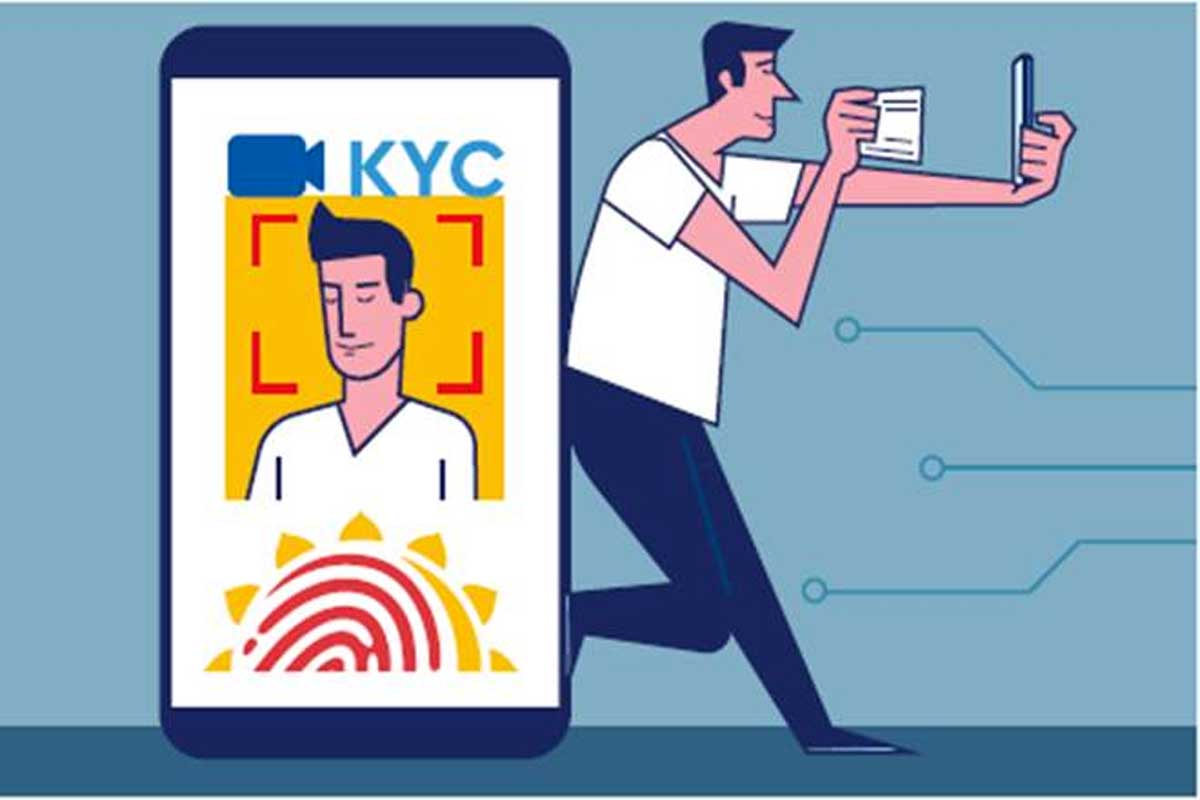
KYC processes are the backbones of a financial institution’s anti-money laundering efforts. Find out how businesses are revolutionising the long, tiresome process.
Know Your Customer or KYC processes are the backbones of a financial institution’s anti-money laundering efforts. According to current estimates, the amount of KYC spending rose to up to $1.2 Billion in 2020 on a global level.
With a whopping amount as this being spent on making KYC processes better, it is easy to assume that the process would be unhackable and issues-free. But inspite of the importance of the process, KYC continues to operate inefficiently. Clenched by labor-intensive and time-consuming tasks, the high scope of effort duplication, and the risk of error, it is estimated that 80% of KYC efforts go on gathering information and processing while only 20% of efforts are assessing and monitoring focused.
While the current KYC process is failing to serve its purpose on the financial institution front, the tiresome, long, and repetitive process is creating an annoying experience for customers.
A hopeful respite to the situation comes from the fact that several financial institutions and service providers are trying to solve the issues by the way of incorporating new-gen technologies like cognitive technologies and AI.
In this article, we are going to delve into a technology that we believe carries the key to eliminating efficiencies and duplication in KYC processes – Blockchain.
In order to truly understand the changes that Blockchain can bring to the counterproductive KYC process, it is important to understand the problem areas of the present system. The problems will help us understand how blockchain technology for KYC is becoming a necessity.
The Lags in Centralized KYC Systems

Every bank or financial service provider comes with its individual set of specifications with no standardization. This often results in users performing the KYC process with every bank and provider they use. Moreover, a tight siloed system like this limits FIs from tracking consumers’ expenses on other platforms – leading to every institution having their specific set of incomplete data.
This centralization of data in silos combines to cause an inefficient KYC process. One that creates issues like:
- Misidentification of fraudulent data
- The inability of tracking customers
- Customers entering fake data
- Delayed processing time
The result of these challenges is spending numbers that we mentioned earlier and a constant rise in money laundering instances.
As a way of changing the situation, the KYC process is gradually being shifted to Blockchain. Let’s deep dive into the process of using Blockchain for KYC verification and the benefits that the movement offers to the fintech sector.
The Blockchain KYC Process
The process of using Blockchain for KYC happens through multiple stages in a Distributed Ledger Technology.
Let us give you a high-level understanding of the steps of how can Blockchain help KYC.
Step 1: The user builds a profile on the KYC DLT system

Financial Institution (FI) deploys a Blockchain-based KYC platform which the user completes as a one-time setup using their identity documents. Once uploaded, the data become accessible to the FI1 for verification purpose.
There are multiple options when it comes to storing the users’ data:
- A centralized, encrypted server
- On F1s private server
- DLT platform.
Step 2: User performs transactions with FI1

When the user performs a transaction with FI1, they give them the right to access the users’ profile. The FI1 then verifies the KYC data and saves a copy of the data on their server. Next, they upload a ‘Hash function’ on the DLT platform.
Finally, FI1 transfers KYC digital copies to the user’s profile embedded with a Hash Function which matches the Hash Function uploaded on the DLT platform.
Now, if the KYC data is altered, the Hash Function of the KYC data won’t match the one posted on the DLT platform alerting the other financial institutions on the blockchain of such change.
Step 3: User performs a transaction with FI2
When FI2 asks the user to perform KYC, the user grants access to their user profile to FI2. FI1 then reviews the KYC data (and its Hash Function) with the Hash function uploaded by FI1. If the two matches, FI2 would know that the KYC is the same as the one received by FI1.
In case the Hash Functions don’t match, FI2 would have to manually validate KYC documents.
But what happens when the user obtains a new passport or driver’s license and their original document in DLT user profile changes?
In such cases, financial institutes leverage smart contracts for automatically updating their systems when the user provides new documents. Here too, the user submits the new document to F1 who then broadcasts the change across the blockchain (through the new Hash Function) which then becomes accessible to other FI participants.
The benefit of a Blockchain solution for KYC can be seen in:
- Data Quality: all data alterations are tracked and monitored in real-time
- Lowered turnaround time: through KYC Blockchain software solutions, FIs get direct access to the data which saves data gathering & processing time
- Reduced manual labor: KYC on Blockchain eliminates paperwork from the process.
The benefits of KYC Blockchain implementation cannot be limited to these points. There are a number of sector benefits that the process of KYC using Blockchain offers.
Benefits of Blockchain in KYC/AML Process
The use cases of the decentralized technology in KYC technology is not just a Blockchain in Fintech offering. There are a number of sectors that are partnering with a Blockchain development company to explore the application.
Distributed data collection
The introduction of blockchain in KYC brings data on a decentralized network which can be accessed by parties after permission has been given to them. Moreover, the system offers efficient data security since the data can only be accessed after permission has been given by the users, thus eliminating instances of unauthorized access.
Better operational efficiency

The abilities like an unhackable digital process and sharing user information on a permissioned network can massively lower the effort and time needed in the early stages of KYC. This, in turn, expedites the customer onboarding time and lowers the regulatory and compliance expenses.
Validation of information accuracy
KYC Blockchain systems enable transparency and immutability that, in turn, allows financial institutions to validate the trustworthiness of data present in the DLT platform. The decentralized KYC process acts as a streamlined way for gaining secure and swift access to up-to-date user data. This lowers the labor-intensive efforts that an institution puts behind gathering information.
Real-time updated user data
Every time a KYC transaction is performed at a financial institution, the information is shared within a distributed ledger. This Blockchain technology KYC systems enable other participating institutions to access real-time updated information with a guarantee that every time there’s a new addition in the documents or there are any modifications, they’ll be notified.
Is Blockchain Development Solutions the Answer to KYC Issues?
Gathering information and processing it takes up a great amount of cost, time, and effort in the KYC process leaving very few resources available for monitoring and assessing user behavior for anomalies. By offering speedy access to up-to-date data, blockchain KYC solutions can lower the time needed for the laborious tasks, which, in turn, can be employed to find solutions to more complex KYC challenges.
However, blockchain cannot solve all the issues faced by KYC. After the data is acquired, financial institutions still have to validate the information. For this, AI and cognitive processing-like technologies have to be employed for greater efficiencies.
In its present state, blockchain when used in combination with other technologies can showcase high potential to help institutions lower the cost and time linked with the KYC process.
If you want to explore this side of Blockchain development services or are seeking to validate your decentralized KYC-based idea, get in touch with us – one of the leading blockchain development companies in USA.





































![The Top 5 Sites for Employer Reviews & Ratings [2020 Update] | Ongig Blog](https://d2shvezvv4hf5p.cloudfront.net/wp-content/uploads/2016/06/02080253/top-employer-review-sites-cover-Ongig.png)